Launching this month, Dr. Farahmandi’s lab, the Silicon Design and Assurance Lab (SiLDA) opened its doors for students and fellows to study and collaborate in Malachowsky Hall. This lab will serve as an incubator facilitating the development of groundbreaking, interdisciplinary work.
Housed in the new Malachowsky Hall for Data Sciences & Information Technology, the SiLDA Lab offers the latest technology and equipment designed for testing and hardware assurance.

Our Main Research Field
Over the past decades, integrated circuits (ICs) have become ubiquitous in numerous applications ranging from high-end data centers to low-power terminals. On the other hand, the security and assurance of microelectronic systems become paramount to preserve the confidentiality, integrity, and availability of sensitive data, calling for more and more research efforts from both industry and academia. At the University of Florida, the Silicon Design and Assurance Lab (SiLDA) led by Dr. Farimah Farahmandi strives to develop cutting-edge solutions for assessing security vulnerabilities of IC designs and enhancing system resilience against the most threatening attack vectors.

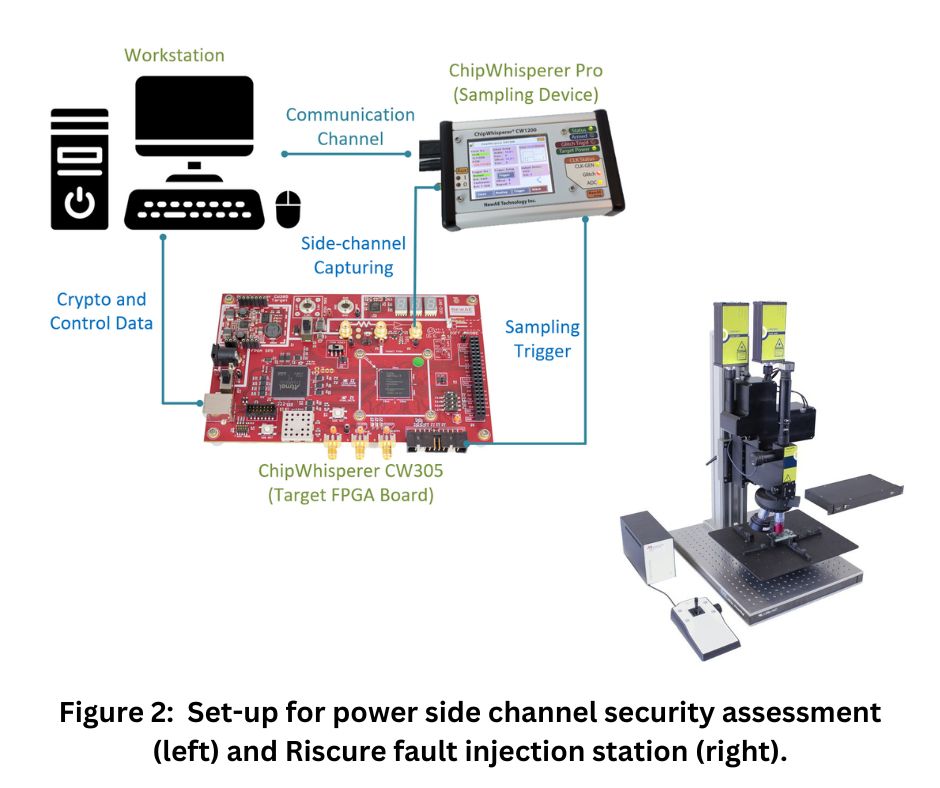
Cutting Edge EquipmentOur lab (lab 3229 in UF Malachowsky Hall) is equipped with leading security inspection instruments and experts with analysis capabilities including but not limited to (i) Security bugs emulation. For timely security closure, we have the Synopsys ZEBU emulation platform. It consists of reconfigurable devices which can accommodate the logic of the most recent processors such as Apple CPUs or Nvidia GPUs. As such, the security verification can be confirmed on real silicon while being accelerated by orders of magnitude. (ii) Medical device security. The security of medical devices greatly impacts the life safety of patients. We investigate the potential effects of physical disturbance (e.g., EM emissions from smartphones) on critical devices such as heart pacemakers. (iii) Side-channel security. Side-channel attacks can non-invasively deduce security assets from the physical properties (e.g., power, electromagnetic) of a running IC. Our lab has the pre-silicon and post-silicon platforms to prototype arbitrary cryptographic implementations for both power and EM side-channel vulnerability quantification. Specifically, our lab is equipped with quite a few ChipWhisperer instances (CW305, CW Pro, etc.) and Langer EM probing instruments (e.g., RF-K 7-4 H-field probes) for power and EM side-channel security verification, respectively.(iv) Fault injection security. Fault injection attacks can effectively compromise data and system integrity during run-time. For the security assessment of such attacks, we have a Riscue laser station to enable most fine-grained bit-flips on target devices. (v) Testing and probing for security verification.
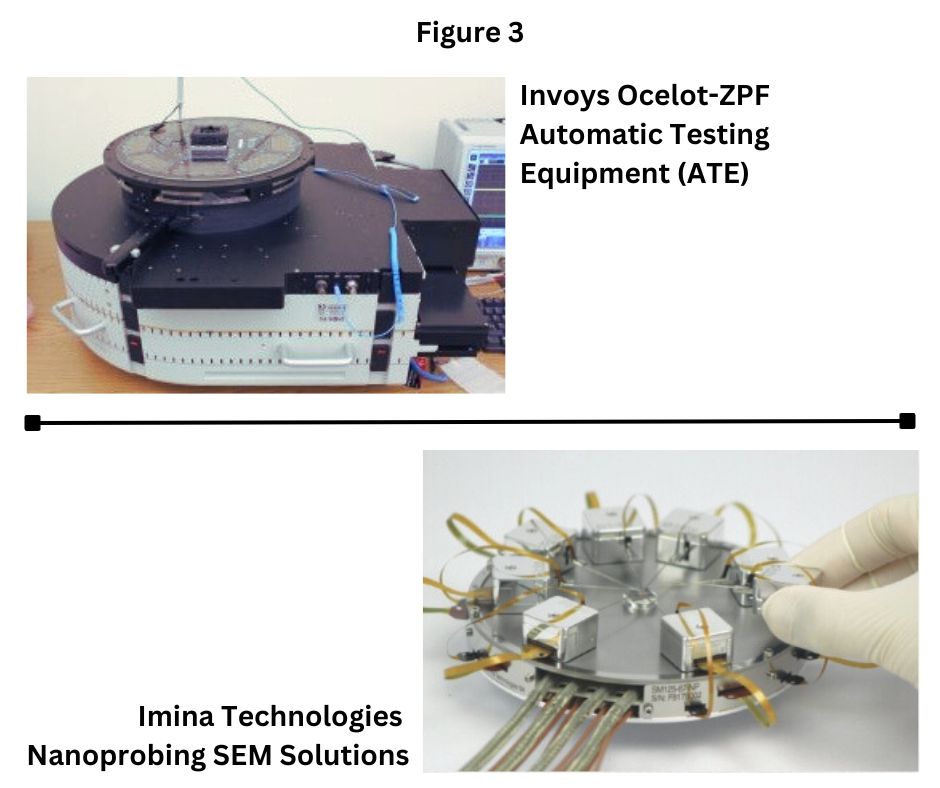
The SiLDA Lab also has the capability to identify security vulnerabilities from post-silicon (commercial-off-the-shelf) devices through testing and probing instruments. Feeding directed test vectors or directly inspecting the internals of suspected ICs using our techniques minimizes the possibility of vulnerabilities to escape.

Open House SiDA Lab: Doctoral student, Dipayan Saha, discusses Synopsis ZeBu Emulation Platform with a curious visitor. Nov. 2023